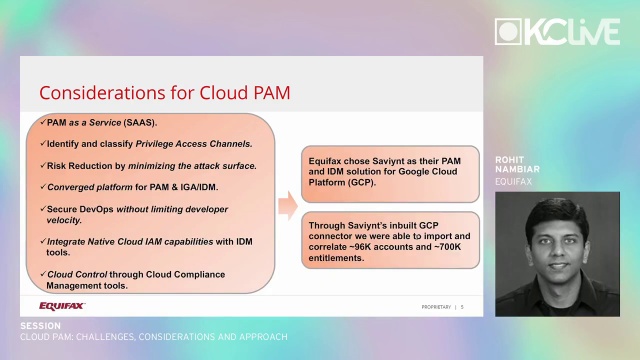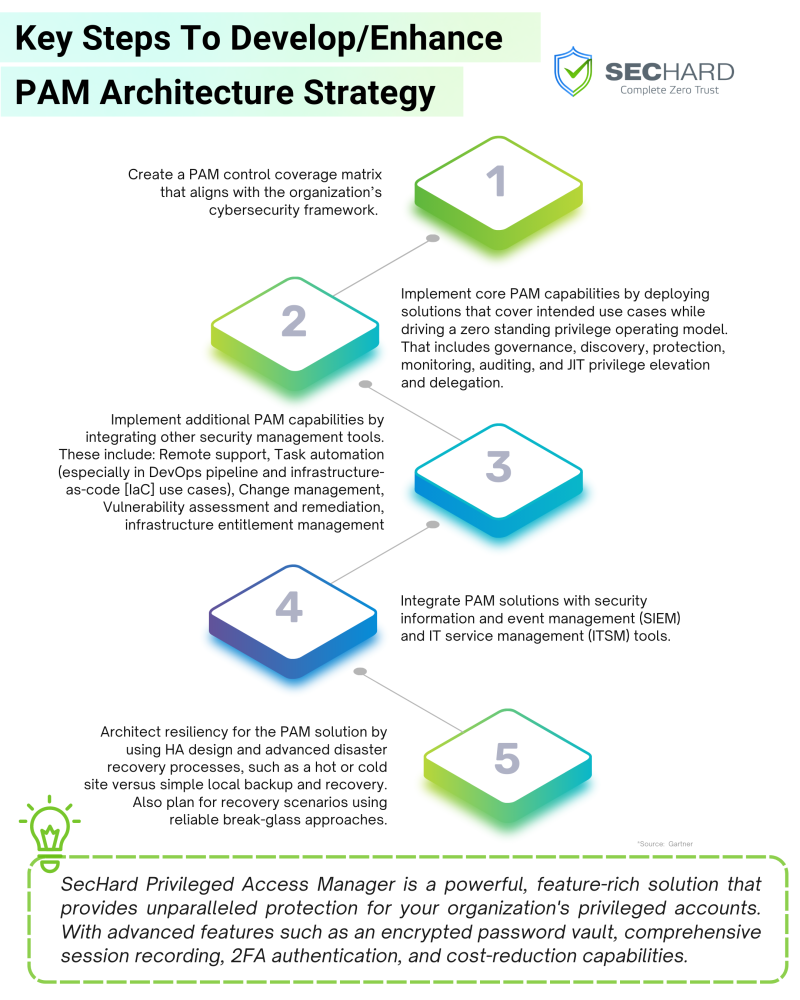
A Comprehensive Guide to Developing an Effective PAM (Privileged Access Management) Architecture Strategy - SecHard

Global Privileged Access Management (PAM) Tools Market Size, Analyzing Growth and Forecasting Outlook from 2023-2030

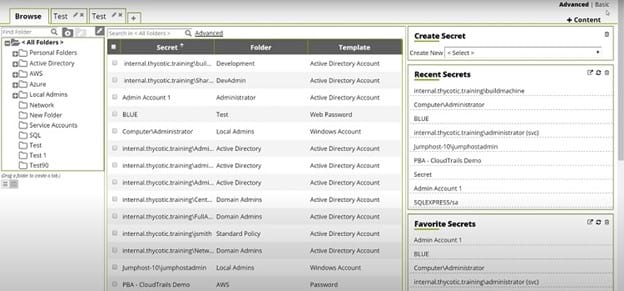
PAM tool: Overview module displaying several widgets (Overdue, Next 7... | Download Scientific Diagram